In the world of Infrastructure as Code (IaC), security is one of the most critical components of the software development lifecycle. Misconfigurations and inadequate access control can lead to security breaches, operational inefficiencies, and non-compliance with regulatory standards. StackGen addresses security head-on, incorporating least-privilege access controls and flexible Identity and Access Management (IAM) policy enforcement directly into the IaC generation process.
Least-Privilege Access Explained
The principle of least privilege access is foundational to cybersecurity. It ensures that users, systems, and services are granted only the permissions necessary to complete their tasks–No more, no less. We can enforce the least privilege in our cloud environment by leveraging IaC to reduce attack surfaces and minimize the risk of unauthorized access to sensitive resources.
Occasionally, developers building cloud infrastructure using IaC may create overly permissive roles or fail to configure fine-grained access policies, leaving the infrastructure vulnerable to exploitation. Least-privilege access ensures that even if a system is compromised, the potential ‘blast radius’ of damage is significantly reduced by limiting the scope of access.
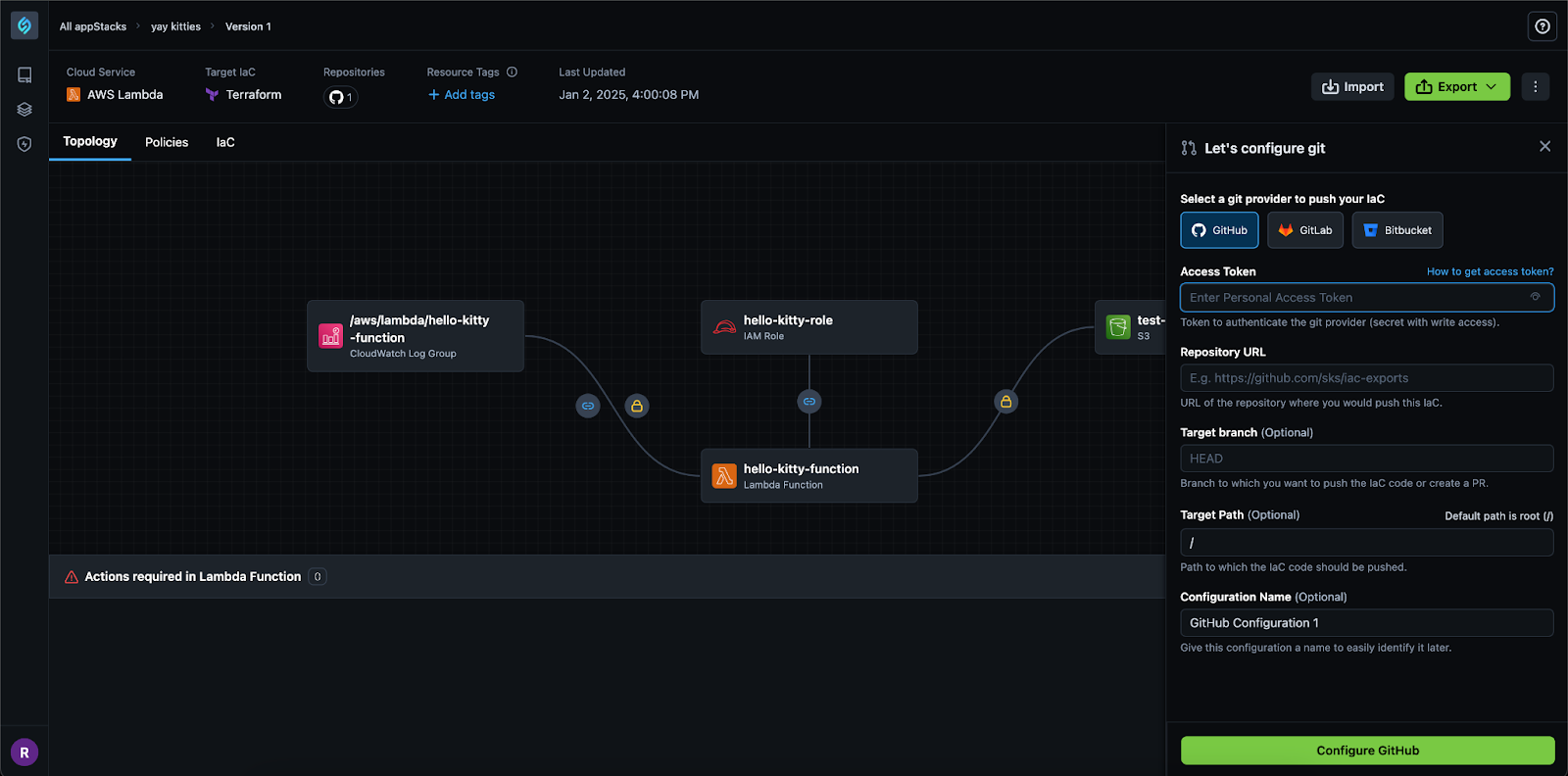
With StackGen, identities within your cloud environment can have their roles configured on an organization-level policy, by team, or by other custom configurations. IAM policies and roles for your cloud (AWS, Azure, or GCP) can be updated as needed to suit a company’s needs and imported directly into StackGen Cloud. User can then export their IaC templates which include least privileged IAM directly to GitHub, GitLab, or BitBucket.
Implementation of least-privilege access controls and fine-grain IAM policies is essential for reducing security weaknesses and maintaining compliance in modern IaC workflows. By aligning role-based access control with robust organizational policies, teams can minimize security risks without compromising agility. Implementing these measures not only safeguards infrastructure, it simplifies governance, making it easier for DevOps professionals and cloud architects to scale their operations with confidence. As infrastructure and deployment complexity grows, adopting security-focused practices is foundational to building resilient, efficient cloud environments.
Simplifying IAM Policy Enforcement
IAM policies are the backbone of modern, secure cloud infrastructure. These policies dictate who can access what resources, and what, if any actions they can perform. Configuration and enforcement of IAM policies manually can be a daunting task, particularly in complex infrastructure environments with multiple cloud providers where teams are doing multiple deployments per day.
StackGen simplifies this process by automatically generating IAM policies that align with least-privilege access principles. By applying these policies at the point of IaC generation, compliance and security are ensured from the first deployment to the last. StackGen also supports the importing of custom IAM policies, allowing for organizations to enforce their own standards and regulatory requirements tailored to their needs.
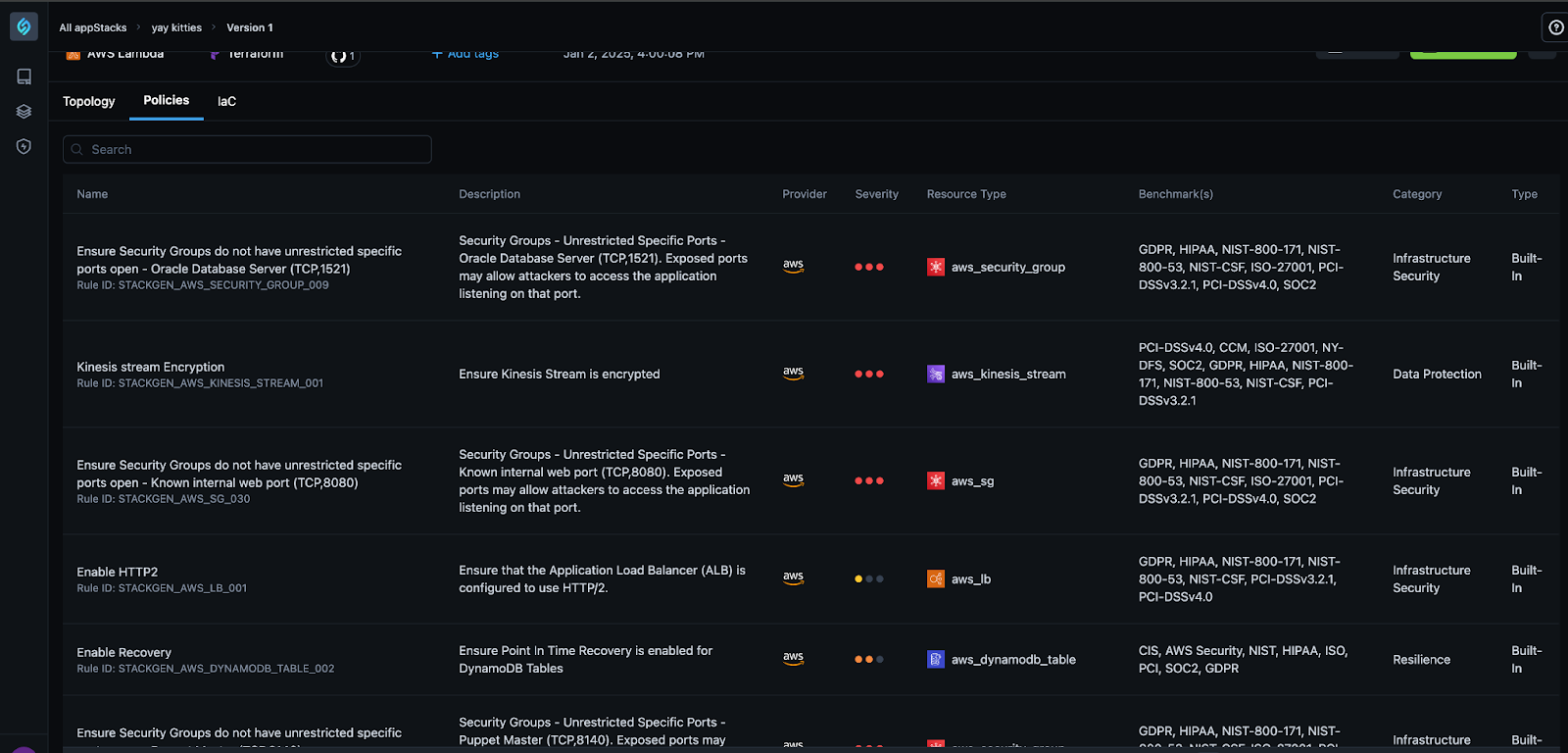
This flexibility is particularly useful for large enterprises with stringent compliance requirements, such as healthcare, financial services, or government sectors. By enabling control over IAM policies, StackGen reduces the risk of IaC misconfigurations while streamlining the software development process.
Resource Mapping and Restrictions
In large-scale development environments, developers may inadvertently provision or connect to unauthorized resources. With the ability to override resource mapping, StackGen addresses this issue before it becomes a problem. This feature ensures that resources are only accessible or connected to by authorized users, based on pre-defined configurations. By standardizing resource mapping configurations across teams, StackGen eliminates inconsistencies and enforces best practices automatically.
For example, if a team is building an application requiring database access, StackGen ensures the application can only connect to the designated database instance and not to other unauthorized resources within the application or environment. This helps prevent potential data leaks and ensures that developers adhere to their organization’s policies while still being able to access the resources they need to complete their work effectively and efficiently.
By implementing least privilege access controls, automating IAM policy enforcement, and standardizing resource mappings, StackGen helps software developers and DevOps teams eliminate the risks and complexities traditionally associated with managing complex IaC workflows. This approach minimizes risks, ensures compliance, and empowers teams to focus on innovation.
Ready to see StackGen in action? Contact us today for a demo and discover how our platform can simplify your IaC workflows while elevating your security posture.